Security researchers have discovered a flaw in SIM cards that enables hackers to track mobile phone users. The vulnerability has been active for two years and can be exploited by sending an SMS.
Dubbed Simjacker, the flaw was found by researchers at Adaptive Mobile Security. They said that the flaw has been used by a specific private company that works with governments to monitor individuals.
Researchers said that the flaw is a “huge jump in complexity and sophistication compared to attacks previously seen over mobile core networks”.
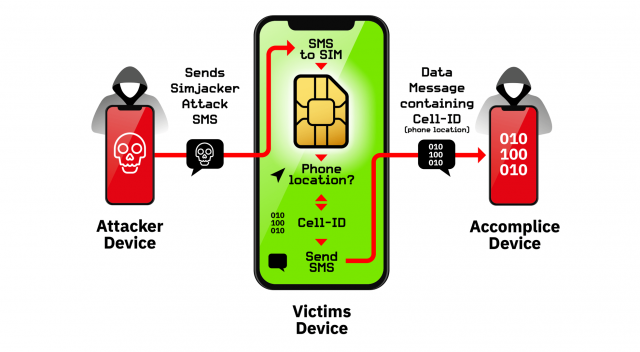
The attack involves an SMS containing a specific type of spyware-like code being sent to a mobile phone, which then instructs the SIM Card within the phone to ‘take over’ the mobile phone to retrieve and perform sensitive commands.
Researchers added that the location information of thousands of devices was obtained over time without the knowledge or consent of the targeted mobile phone users.
“During the attack, the user is completely unaware that they received the attack, that information was retrieved, and that it was successfully exfiltrated. However the Simjacker attack can, and has been extended further to perform additional types of attacks,” warned researchers.
The attack exploits the presence of a particular piece of software, called the S@T Browser (short for SIMalliance Toolbox Browser), that is embedded in most SIM cards.
An SMS message containing the attack (as a Binary SMS used to deliver rich content such as ring tones), is sent to a phone. The device passes the SMS to the SIM card without checking its security; the SIM then executes the commands embedded in the message. The message can command the phone to reveal the location of its user and other information, such as IMEI numbers.
“During the attack, the user is completely unaware that they received the attack, that information was retrieved, and that it was successfully exfiltrated,” the researchers said.
Simjacker can also be used to “perform many other types of attacks against individuals and mobile operators such as fraud, scam calls, information leakage, denial of service and espionage”.
Researchers said that the vulnerability could extend to over a billion mobile phone users globally, potentially impacting countries in the Americas, West Africa, Europe, and the Middle East.
The firm has alerted the GSM Association, the trade body representing the mobile operator community, over the existence of this vulnerability. The flaw has been managed through the GSMA CVD program, allowing information to be shared throughout the mobile community, said researchers.
Jonathan Knudsen, senior security strategist at Synopsys, said that the disclosure of the Simjacker vulnerability once again forces us to confront the fact that any layer of the technology stack might contain surprises.
“Just as Rowhammer and Spectre made us question and examine the basic building blocks of computers, Simjacker shines a light on a novel attack vector at the heart of every mobile device,” he said.
Sam Curry, chief security officer at Cybereason, said that while details are still emerging in this particular breach this would appear to have the makings of a nation-state actor.
“They almost never engage in smash and grab campaigns to steal money, social security numbers or credit card numbers. Their motives are likely to target certain individuals to know who they are talking to, where they are traveling and when,” he said.